To be able to successfully create a connection between Oracle Integration Cloud and Oracle Fusion Apps, for example ERP Cloud, there are some pre-requirements to perform. To be able to connect Integration Cloud with Fusion Apps it is in most cases required to import OAuth signing keys from the OCI IAM used by Integration Cloud into Fusion Apps Console. This article provides a step-by-step guide on setting up these pre-requirements.
Article by: Robert van Mölken
In our last article, we tackled the process of linking Oracle Integration Cloud with Fusion Apps, like ERP Cloud, through OAuth 2.0. As we navigated the setup, we detailed the creation of two confidential applications in OCI IAM to tap into the Fusion Apps Endpoint URL. But before you dive into the Oracle Integration Cloud configurations, there are essential prerequisites to bear in mind. Neglecting these could lead you to grapple with numerous CASDK-0004 errors when you give the connection in Integration Cloud a test run.
Export and import JWK signing keys
Temporarily add Identity Administrator role to Fusion Client (Confidential) App
In our previous article titled ‘How to Create Confidential Applications in OCI IAM for Invoking Fusion Apps Endpoint Using OAuth,’ we discussed the creation of an OAuth 2.0 client application. To enable the retrieval of JWK signing keys, we will need to assign the ‘Identity Domain Administrator’ role to this application within the IDCS (Oracle Identity Cloud Service).
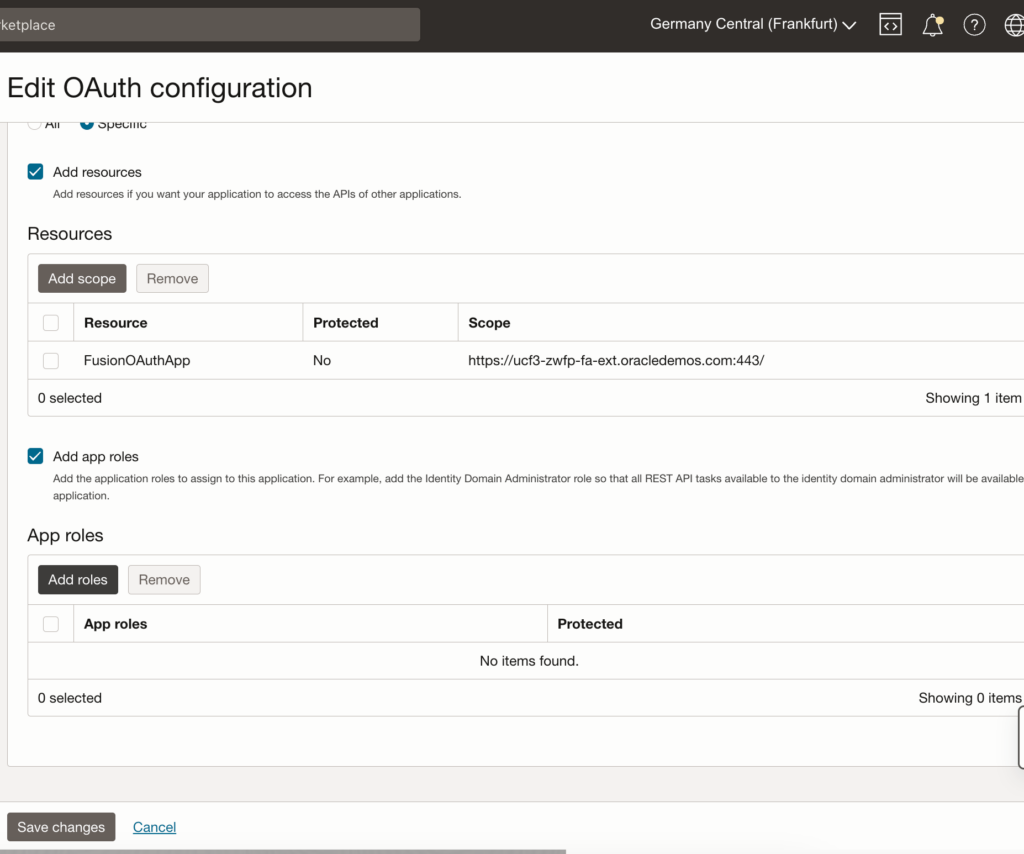
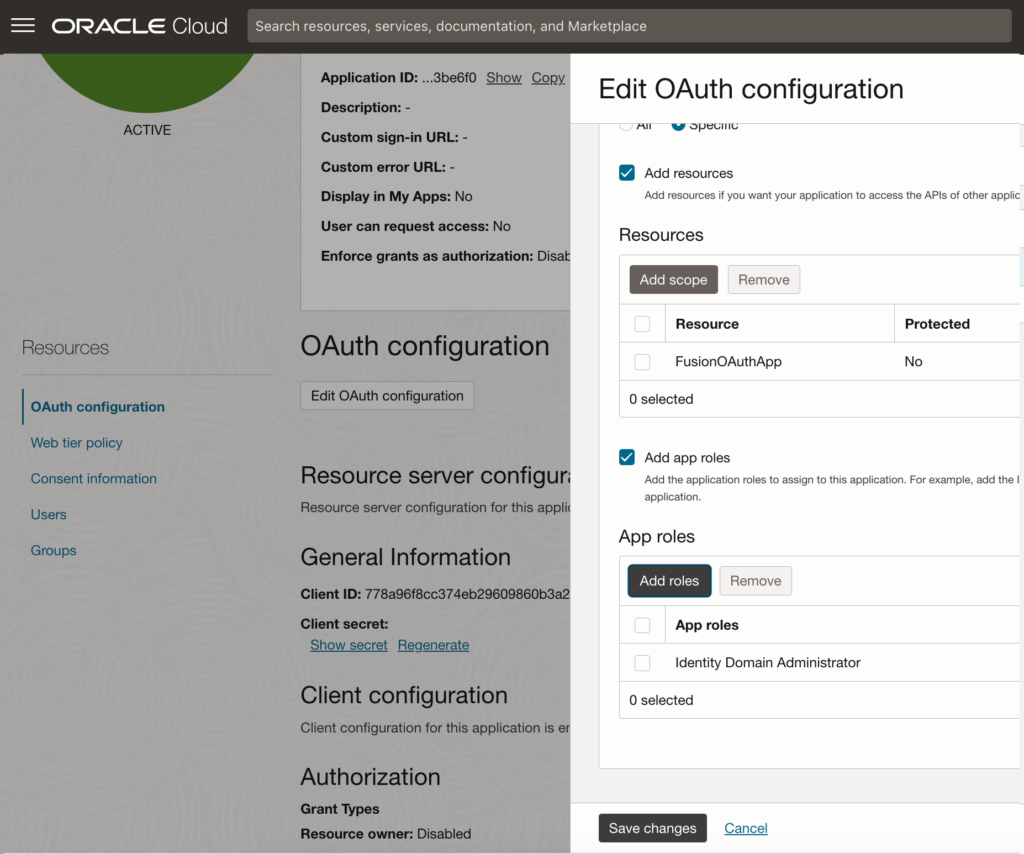
To accomplish this, follow these steps to edit the OAuth configuration for ‘FusionClientApp‘:
- Check the ‘Add app roles‘ checkbox.
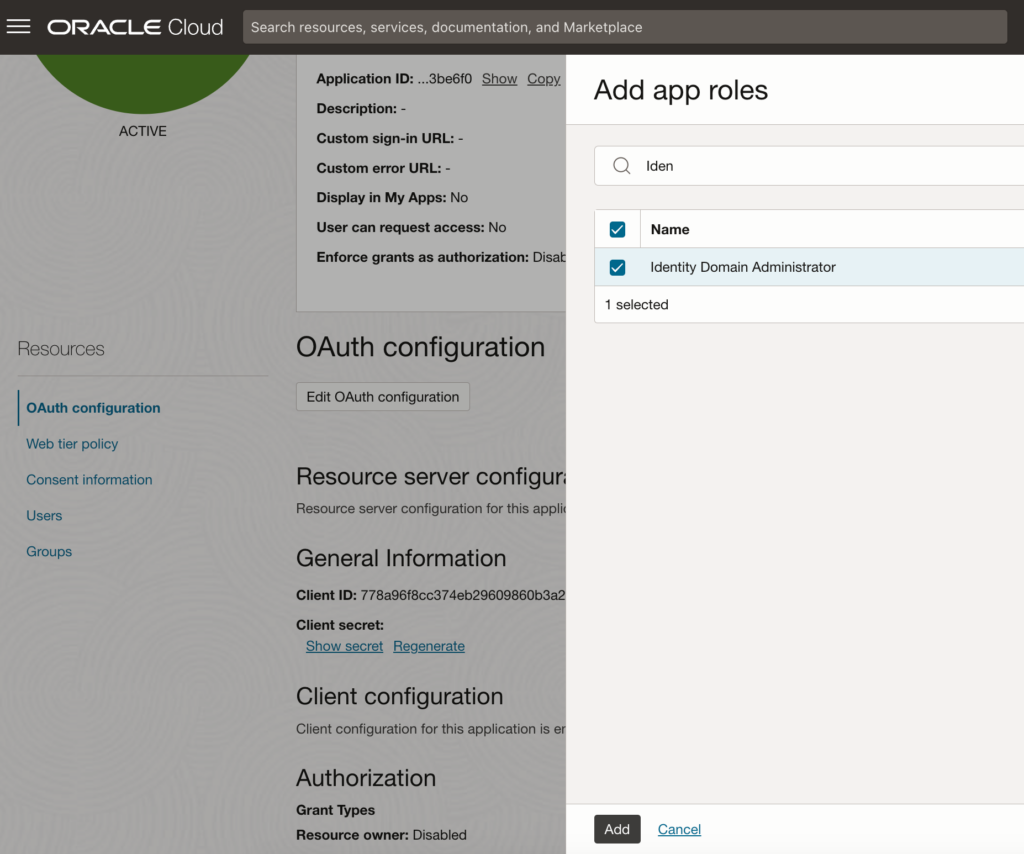
- Click the ‘Add role‘ button. This action will open a side-panel where you can search for and add roles.
- Search for ‘Identity‘ and select the ‘Identity Domain Administrator‘ role.
- Confirm the selection by clicking the ‘Add‘ button.
- After adding the role, remember to save the changes to finalize the configuration.
Please don’t forget to remove it when it is no longer needed at the end of the process.
Export JWK signing keys from OCI IAM
To obtain the signing certificates used by JWK (JSON Web Key), a JavaScript Object Notation (JSON) data structure representing a cryptographic key, you can utilize a REST API provided by IDCS (Oracle Identity Cloud Service).
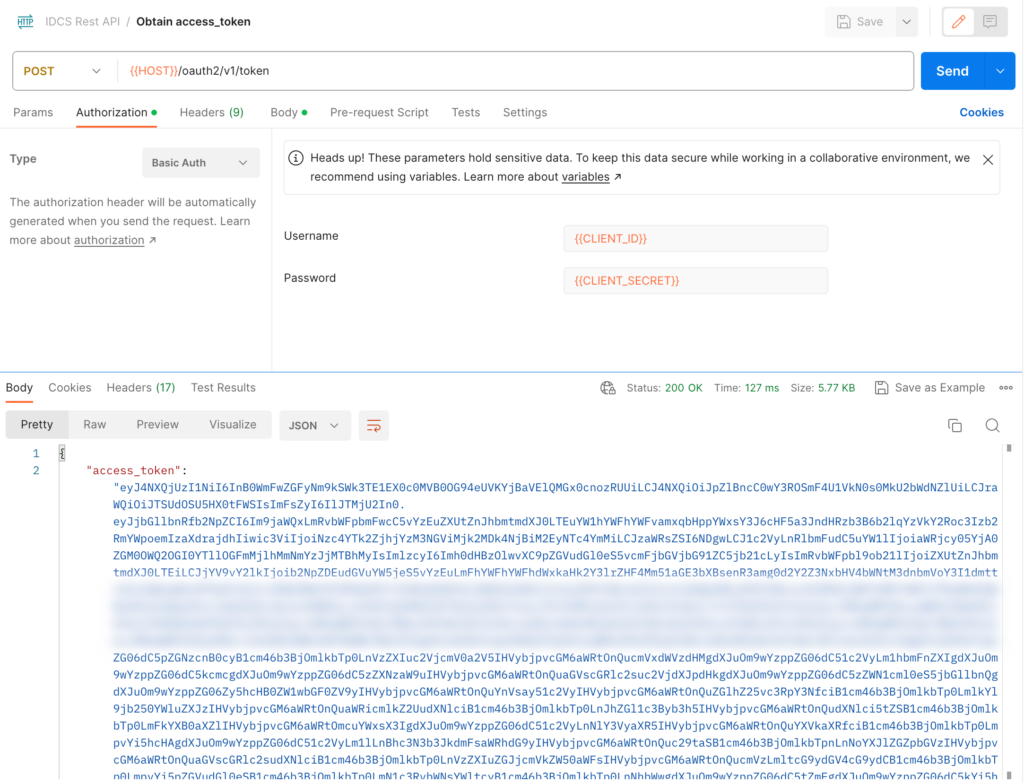
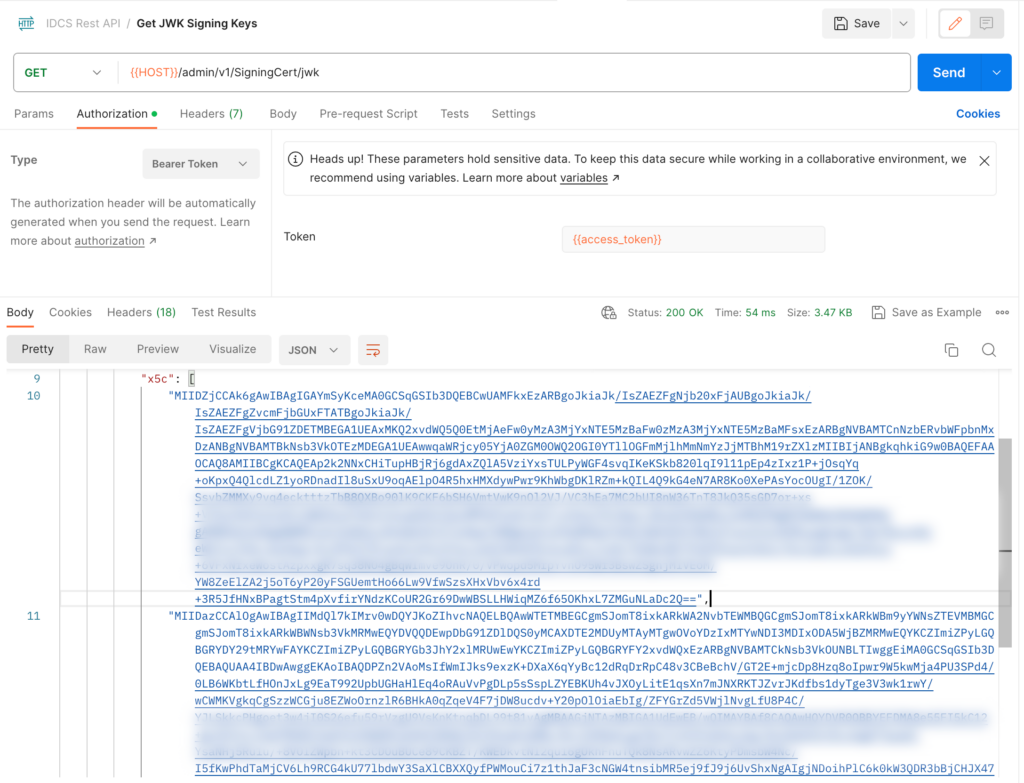
The REST endpoint is designed to retrieve the Tenant’s Signing Certificate in JWK Format. It utilizes the API resource path /admin/v1/SigningCert/jwk, which must be preceded by the IDCS domain URL. The most convenient method for fetching these keys is by using Postman and making a GET request to the complete URL. It’s worth noting that the IDCS REST API requires an OAuth token for authentication. Therefore, prior to calling the SigningCert API resource, you’ll need to obtain an OAuth access token using the token URL with the resource path: /oauth2/v1/token.
The first image depicts a GET request to the resource, executed in Postman, using the client ID and secret of the OAuth confidential application, such as FusionClientApp.
To acquire the SigningCert keys and format the certificate for uploading it in binary (file) format, you must call the API resource path /admin/v1/SigningCert/jwk. To authenticate with this API, you’ll need to copy the obtained access token and use it as a bearer token, as demonstrated in the second image. The response will contain a set of two keys under the x5c attribute, starting with the phrase MIID. The first key corresponds to the certificate of the IDCS domain, while the second key is the certificate of the signing authority
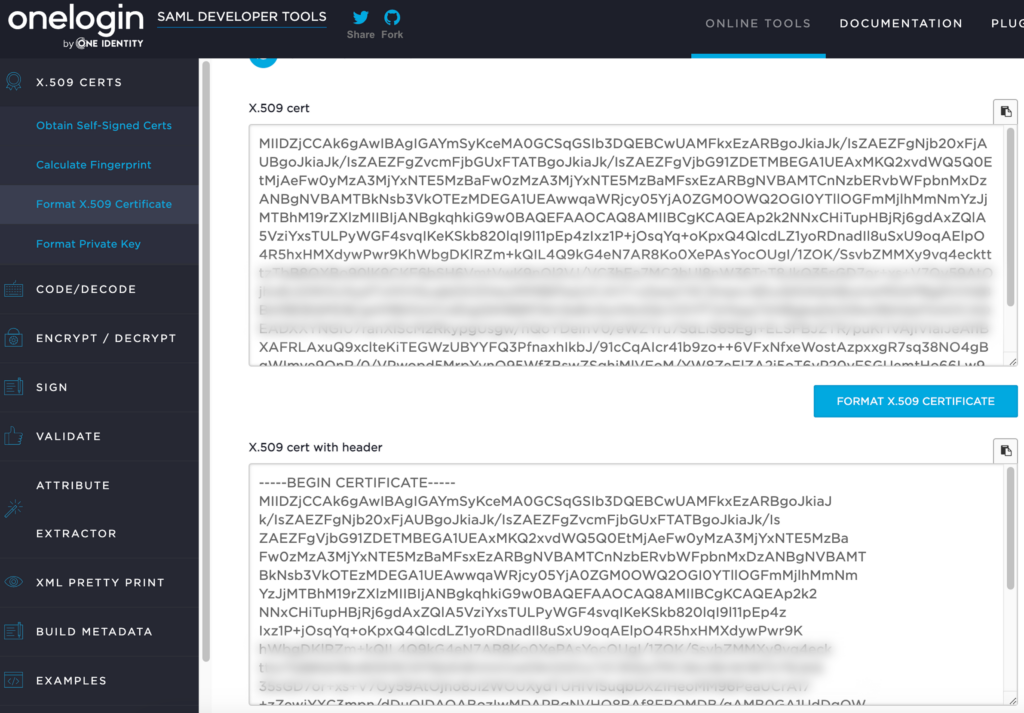
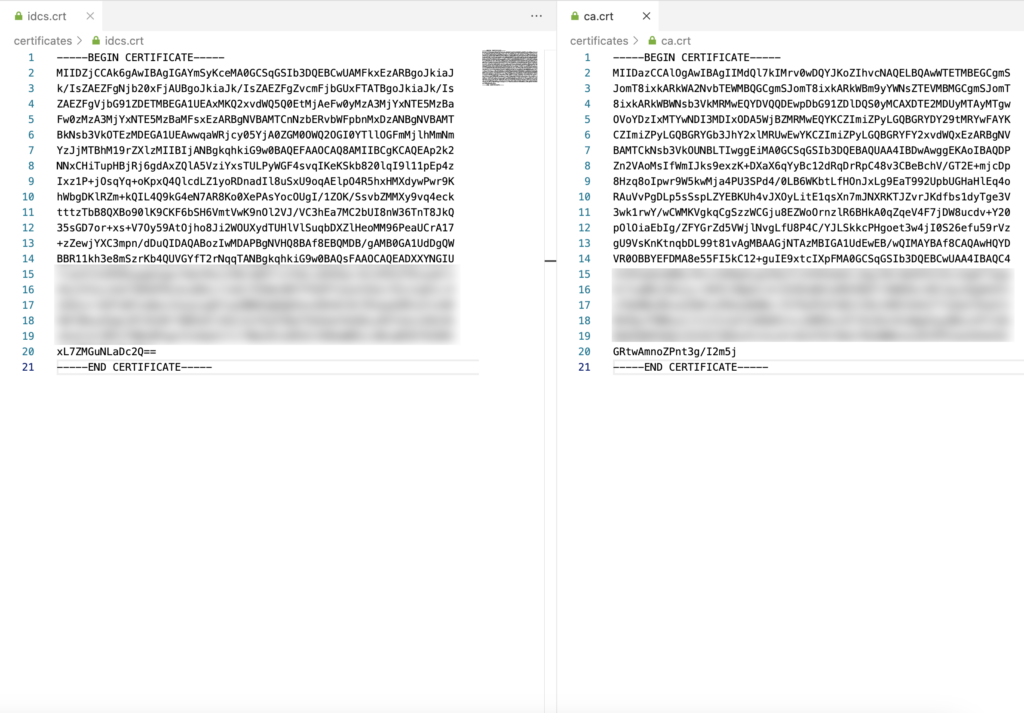
After you retrieved the two keys you need to format each of them correctly to a X.509 certificate. I like to use a browser tool from SAMLtool for this : https://www.samltool.com/format_x509cert.php. This tool formats the string and adds the required header and footer. Store each certificate in its own file e.g., idcs.crt and ca.crt.
Import JWK signing keys into Fusion Apps
The next part of the process is to import the certificates into Fusion App. For you to be able to do this you need to login as “IT Security Manager” in Fusion App, else you are not able to see the Security Console. Below are the steps to complete:
- Login to your Fusion App home URL as IT Security Manager
- Click on the Hamburger icon next to the logo
- Under Tools, click on the option called Security Console
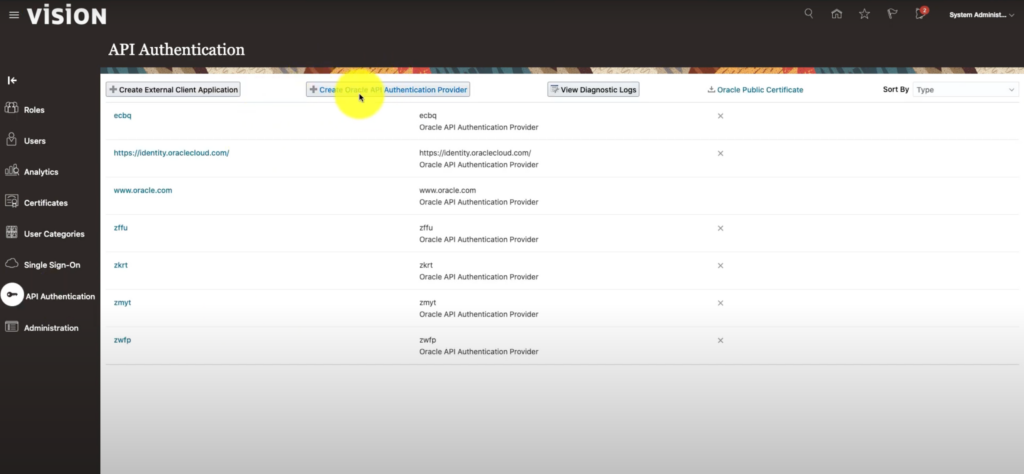
- In the Security Console, navigate in the menu to API Authentication
- The API Authentication page shows all providers, click the Create Oracle API Authentication Provider button
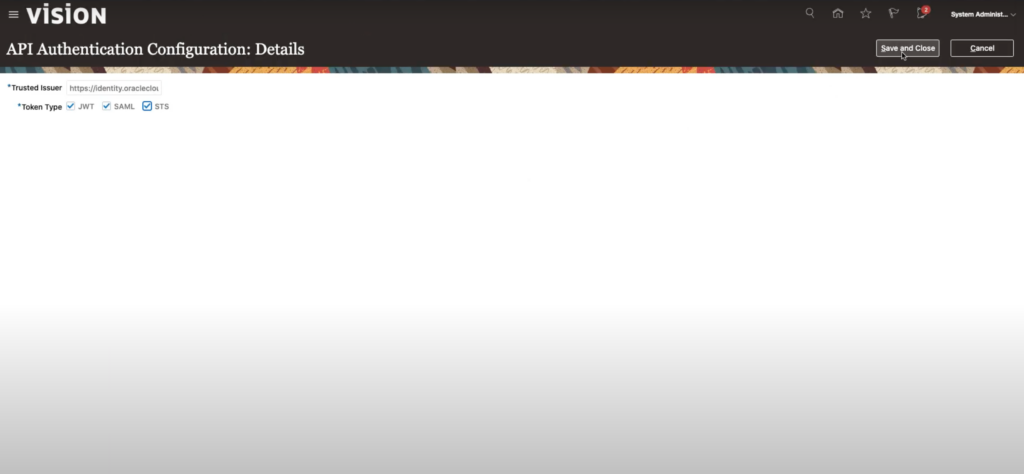
- In the Trusted Issuer field, enter https://identity.oraclecloud.com and press Enter
- Select all token types; JWT, SAML and STS and click Save and Close
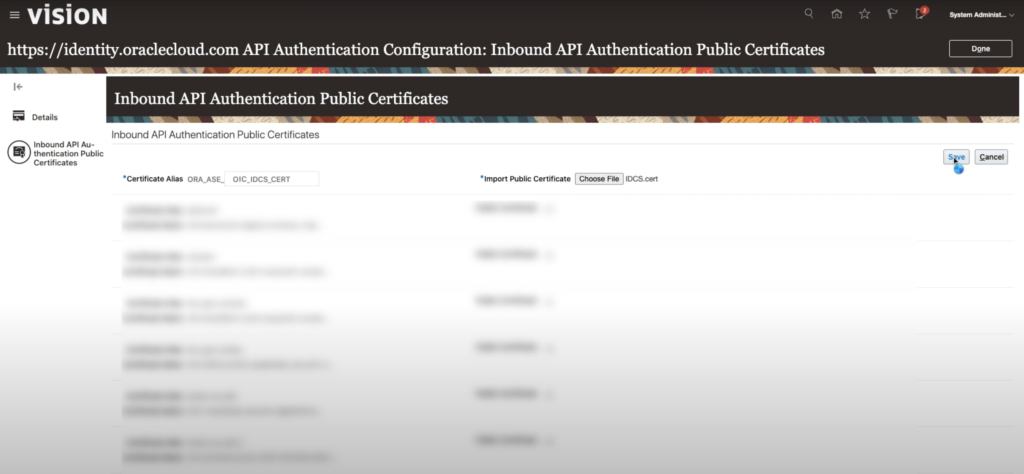
- Click on Inbound API Authentication Public Certificates option on the left sidebar.
- On this page all added certificates are listed, click the Add New Certificate link to add the IDCS certificate
- Enter a Certificate Alias, e.g., OIC_IDCS_CERT, import / choose the public certificate file and click Save
- To the same for the signing authority certificate, enter a certificate alias, e.g., OIC_CA_CERT, choose file and Save
!! Do not forget to remove the Identity Domain Administrator role on the confidential application !!
Create a shadow user in OCI IAM mirroring Fusion App user
Assign the correct integration roles to the Fusion App user
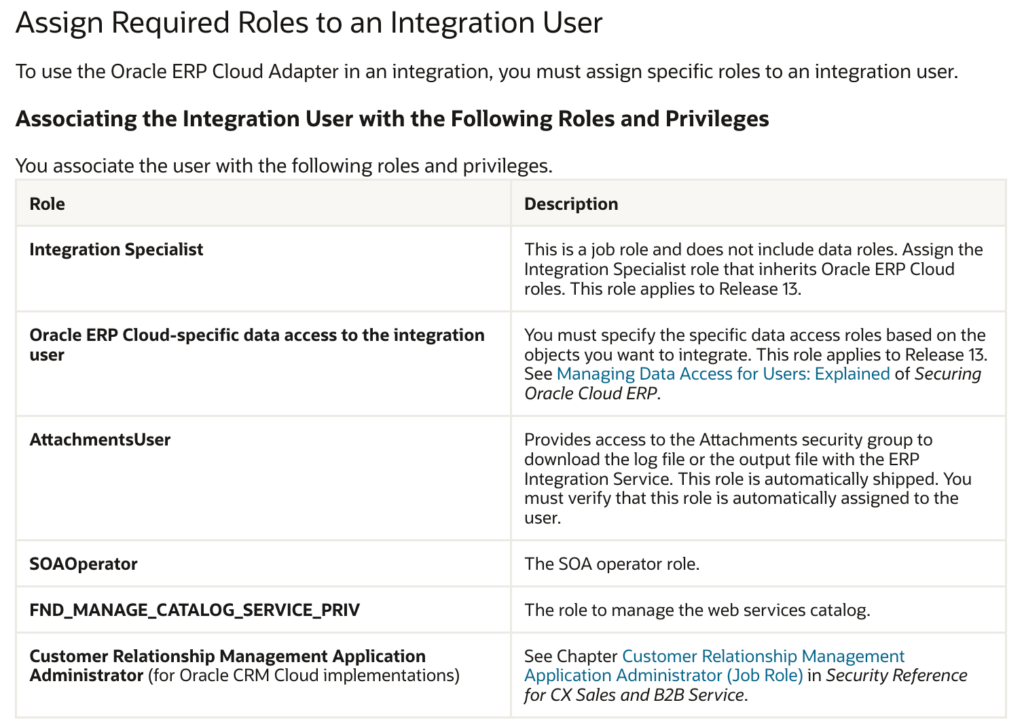
Before proceeding further to ensure that we avoid encountering CASDK-0004 errors during our testing of the Integration Cloud connection to Fusion Apps, we must adhere to the prerequisites outlined in Oracle’s documentation page. This page includes a list of requirements, including the assignment of specific roles to the Fusion App user. Notably, two crucial roles are SOAOperator and FND_MANAGE_CATALOG_SERVICE_PRIV.
If the user does not have them you will run into an error while testing the connection :
CASDK-0004 : Unauthorized [401] Error while connecting to the URL – https://<FA POD>.oraclecloud.com/soa-infra
Authentication Failure. Please check if the credentials provided are valid.